Updated: As of Feb 2022, I have fixed/updated the script so that it runs faster in workgroup computers. The changes as marked in the Changed Log section of the script. Moreover, you can run the script with -WriteVerbose switch to see the execution time.
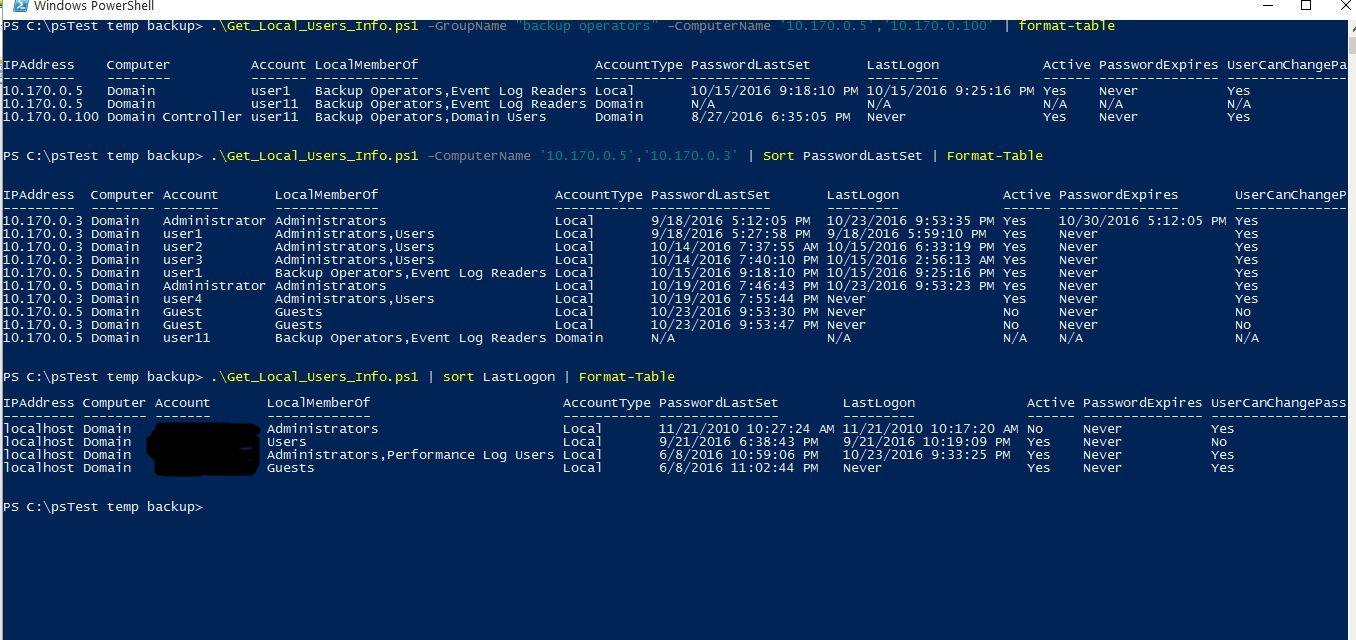
Sometimes, you need to know which users are in local admin group or specific group on remote computers. The windows built-in command Net User give us a good way to get password information for local or domain users. Using net user /domain switch will show the domain group membership info but it will be truncated to 20 characters for long group names. So, I’ll use ‘net user’ output and query the WMI to make a script to find user account & password info in either local or domain environment. Though my example is only on unencrypted winrm connection which listen on port 5985, I suggest to use ssl encrypted for remote winrm connection.
What this script will do:
1) It will test connection on port 5985 if the ComputerName parameter is defined.
2) It will search for local users account, their password info on remote computers.
3) If the GroupName parameter is defined, it will only search for that specific group.
4) You can sort the PasswordLastSet, LastLogon properties to find out the users with oldest password or who never logged into the computer.
5) You can export the result to csv file with
\.Get_Local_Users_Info.ps1 -ComputerName MyComputerName | sort PasswordLastSet | Export-Csv -NoType users_account_info.csv
Note: When we query the domain user’s info on remote computer, there comes a Kerberos multiple-hop problem, in which we need to delegate client credentials to domain controllers, which need additional configuration on both client & server sides before the script runs. Therefore, I put the N/A values when we query the domain account info from remote domain-joined computers. You can learn more about CredSSP here:
https://blogs.msdn.microsoft.com/powershell/2008/06/05/credssp-for-second-hop-remoting/
https://msdn.microsoft.com/en-us/library/ee309365(v=vs.85).aspx
You can download my script from github.
