You can simply check the SSL/TLS certificate information which is listening at non-http port (like STMP) by using the OpenSSL tool. All you need to know is to the port that uses encrypted connection. For example, I view the certificate info at CentOS website & TLS certificate used for smtp connection. With WSL, OpenSSL already installed and you’re ready to go.
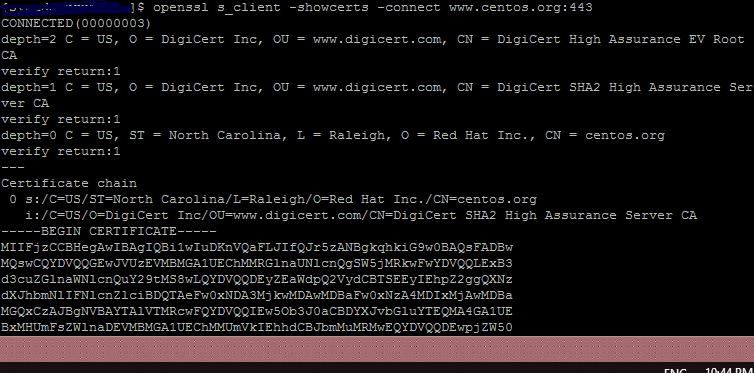
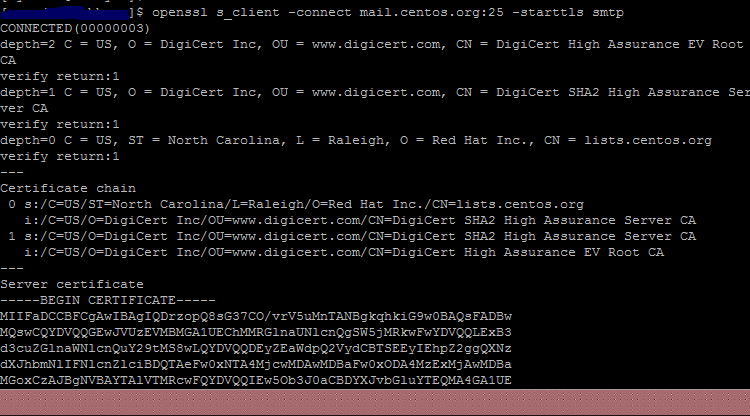
For example here, I check the CentOS website & TLS certificate which is used for smtp connection.
For SSL connection:
openssl s_client -showcerts -connect www.centos.org:443
For TLS connection:
openssl s_client -connect mail.centos.org:25 -starttls smtp