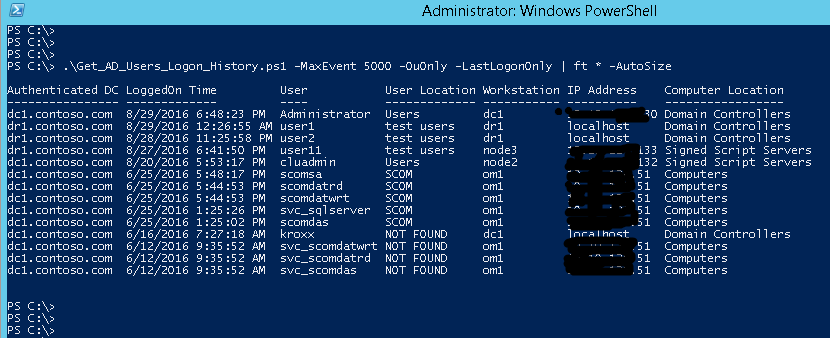
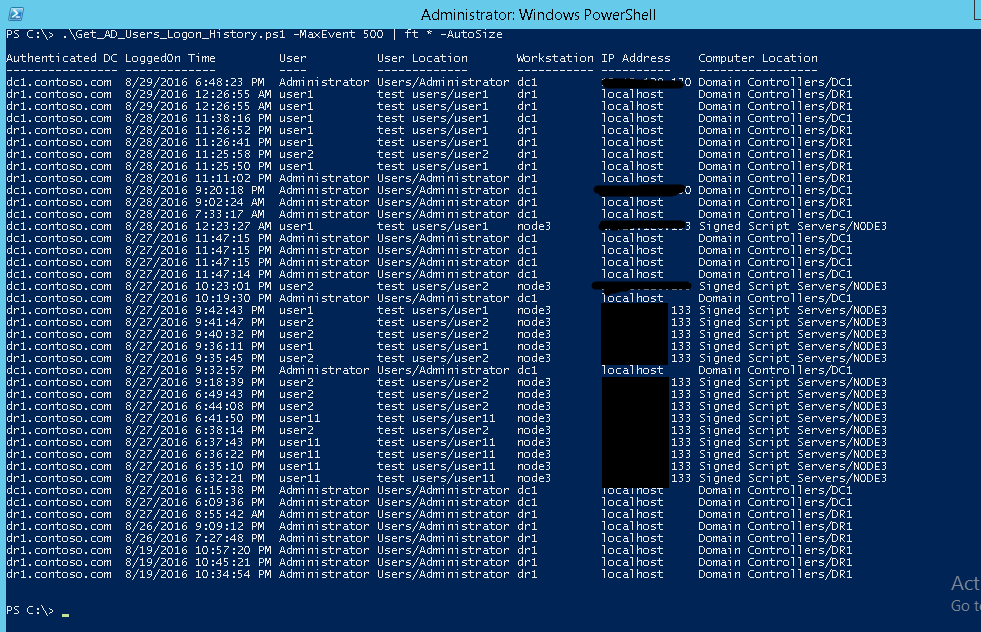
One of the daily system admin task is to check the user login history throughout the domain. It becomes quite a tough task if you have to go through thousands of event logs to find the correct security events of users logon from every domain controllers. Though we filter only the Kerberos Authentication Events for TGT (Ticket-Granting-Ticket) Requests, there are so many information in each event regarding to specific users.
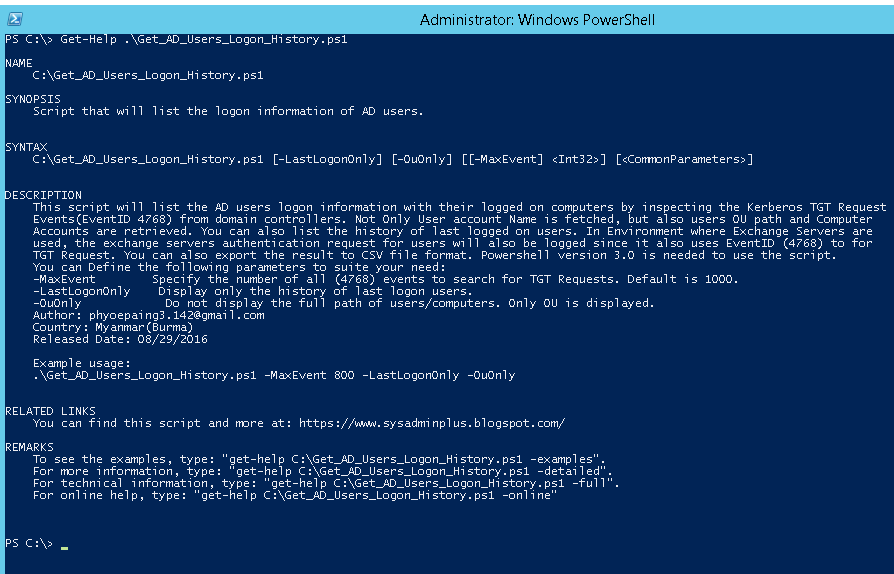
So, I am taking some time to put all these Kerberos events together from every domain controller to look for some useful information and then write this handy script to save my difficult days !
Note: This script contains cmdlets from DnsClient module which needs Server2012 or Server2012R2 to run the script. If you run the script on servers other than domain controller, you need Powershell with Active Directory Module installed. You can check if it is already installed it with the command:
Get-Module *active* -ListAvailable
In environment where Exchange Servers are installed, users requests for TGT also come from exchange servers(Workstation column in our result) occurs when they are authenticated via Outlook Web App.
If permissions error occur or cannot retrieve logs, you may need to “Run as Administrator” Powershell.
Some computers with IP addresses will be shown as “NOT FOUND” if the reverse DNS zone for these computers are not created in AD. For this, you may need to create PTR records for these computers.
You can download my script from github.

Nice script! Is there a way to check only for a specified users?
Is there a way to use archived security event files ? *.evtx ?
Hi! Got this error:
PS C:UsersAdministratorDesktop> .Get_AD_Users_Logon_History.ps1 -MaxEvent 800 -LastLogonOnly
No events were found that match the specified selection criteria.
+ CategoryInfo : ObjectNotFound: (:) [Get-WinEvent], Exception
+ FullyQualifiedErrorId : NoMatchingEventsFound,Microsoft.PowerShell.Commands.GetWinEventCommand
+ PSComputerName : localhost
AD Misconfiguration?