Go to >> Part-2: Request the certificate the sign the script by user1
Go to >> Part-3: Configure GPO to allow only signed scripts and add user1’s certificate to trusted publisher group on domain computers
Go to >> Part-4: Run the test scripts
This is a lengthy post of how to digitally sign your powershell script, so I divide it up to 4 sections. Digitally signing of powershell script, for the security purpose, is particularly useful to prevent the execution of malicious scripts on servers or workstations in your domain environment. Today, I will show you how to sign your powershell scripts from Microsoft CA and use GPO to control the execution of unsigned scripts in domain environment.
Scenario:
Let’s say user1 usually write powershell scripts in Contoso organization. Administrator needs to allow only the execution of scripts written by user1 on certain computers, while other scripts are blocked. Moreover, if one of the user1’s script is modified by a malicious user and run on client computers or servers, how can we stop these things? Let’s see how it works.
My Lab Environment:
DC1 – the domain controller and the one where ADCS role is installed (not recommended to install both roles on single server but for the lab, it’s OK 😉
Node1 – the client computer which user1 will request the certificate for signing his powershell script.
Node2 – the client computer which user 1 script will be run.
As we have to go through many steps for setup. We will break them up into following 4 parts.
- Install ADCS service and configure Code Signing Certificate Template
- Request the certificate to sign the script written by user1
- Configure GPO to allow only signed scripts and add user1’s certificate to trusted publisher group on domain computers
- Let’s test by running some unsigned scripts
Assuming that your domain controller is already setup and Node1 and Node2 are already joined to domain. I’ll install Active Directory Certificate Service Role on DC1 and do some initial configuration.
Open Server Manager >> Add Roles and Features >> Active Directory Certificate Services (For code signing only, you can install Certification Authority with no additional roles). Click Next, Next and Install. Check Figure-1
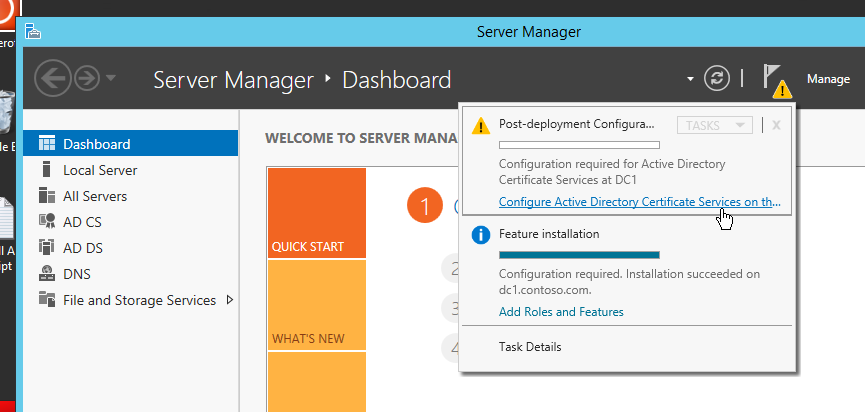
After installing ADCS role, we need to configure for the first Certification Authority setup.
On DC1, click the yellow flag and go through the wizards.
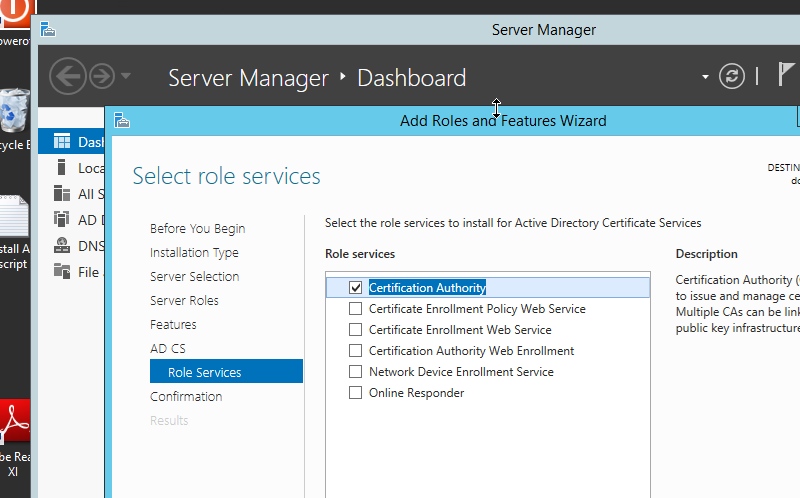
On the “Select Role Services to configure” page, only “Certification Authority” is selected for code signing purpose.
On next page, we choose enterprise CA. It has a good service integration with AD such as certificate auto-enrollment and in our case, all clients needs to automatically trust the root CA which is automatically taken care by Enterprise CA.
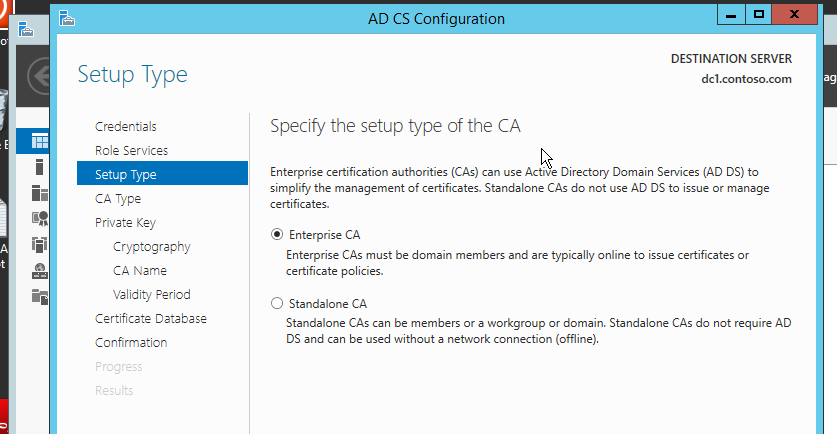
Next page is Root CA or Subordinate CA. Since it is the first CA in our environment, we choose root CA.
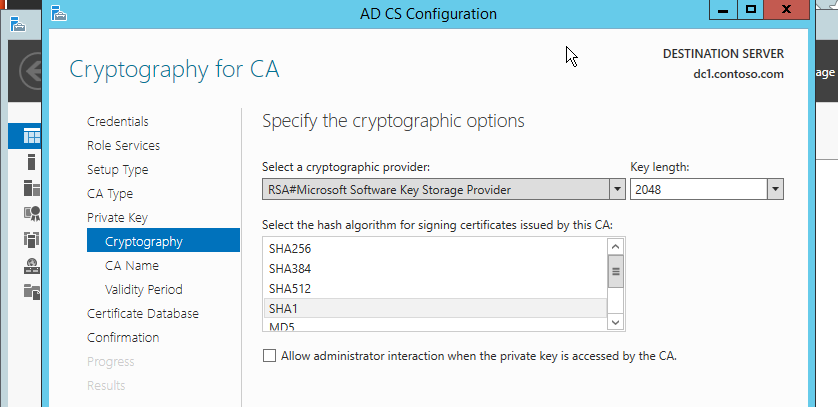
Also, on the new private key page, we do not have a private key yet. So, go with Create a new private key.
Then choose the key length and encryption algorithm to your suite. For me, I go with the default one. See figure-4.
After that, you have to define the common name of the CA and the validity period of the root certificate. Choose default.
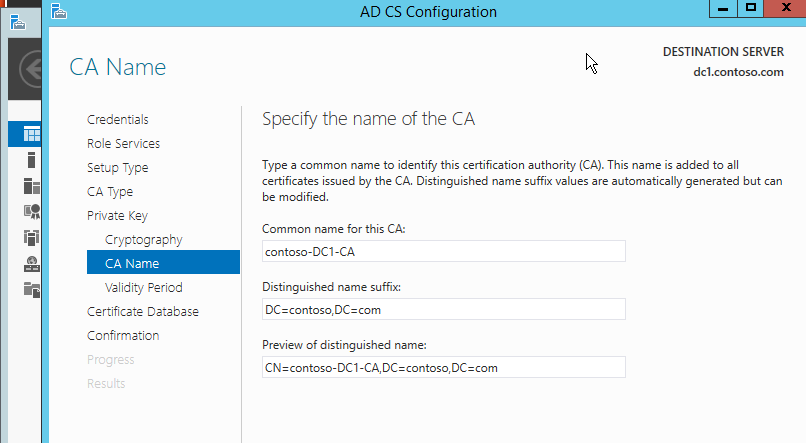
Next page is CA database location and final review. Choose default. And done.
2) Configure Code Signing Certificate from Template
So far, we have done the initial configuration for our CA on DC1 Server. Now, it’s time to configure the certificate we want to issue, the code signing certificate from built-in template. On DC1 Server,
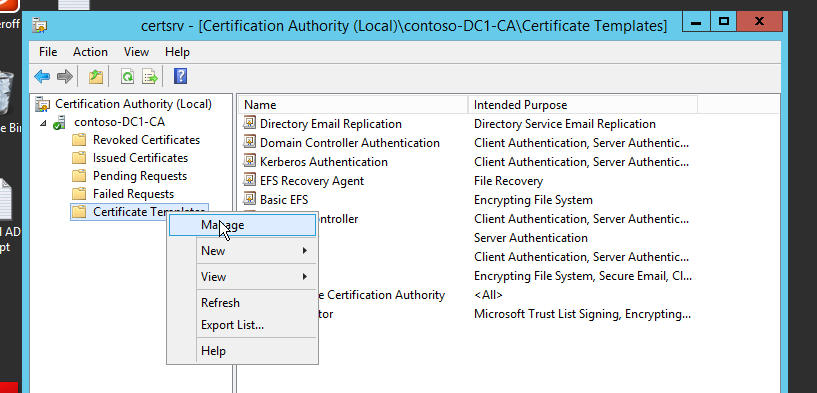
i) Start >> Administrative Tools >> Certification Authority and expand our newly setup CA.
ii) Right-click the certificate template >> Manage. See Figure-6.
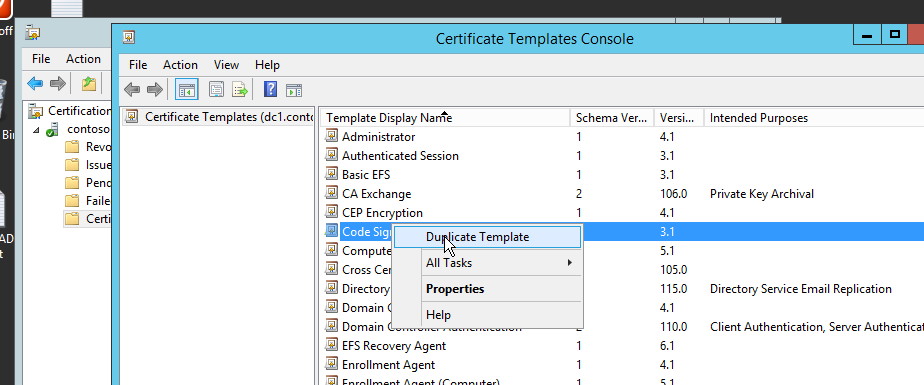
Then there you will find many built-in certificate templates which are readily available to us. For our purpose, we choose Code Signing Template. Like Default Domain Policy, I highly suggest you to duplicate the built-in template rather than editing the original one directly. See Figure-7.
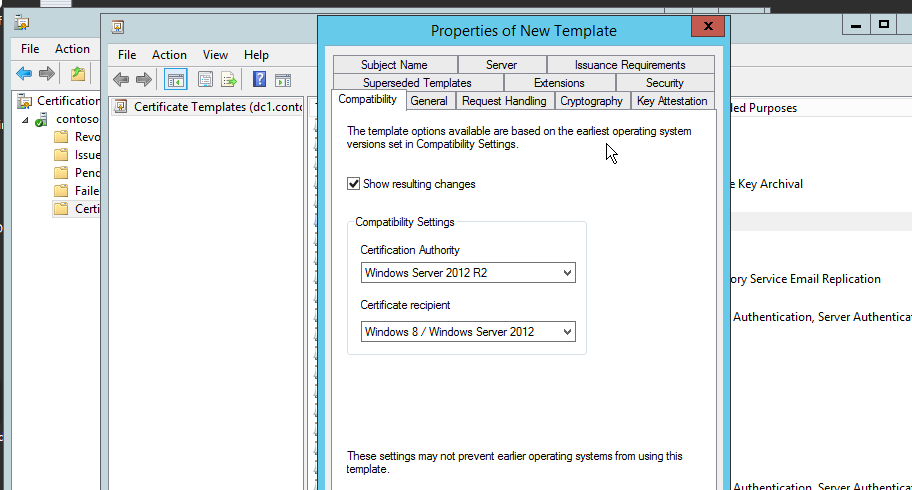
There are some certificate compatibility settings you can choose especially if you have older version of windows and older domain controllers. Unless you have these old versions, you can set both server and client version to the highest level.
Now you have to give user1 the permission to enroll certificate for himself. Since, he has to request the certificate and sign his powershell scripts, he needs to have read and enroll permission on this certificate.
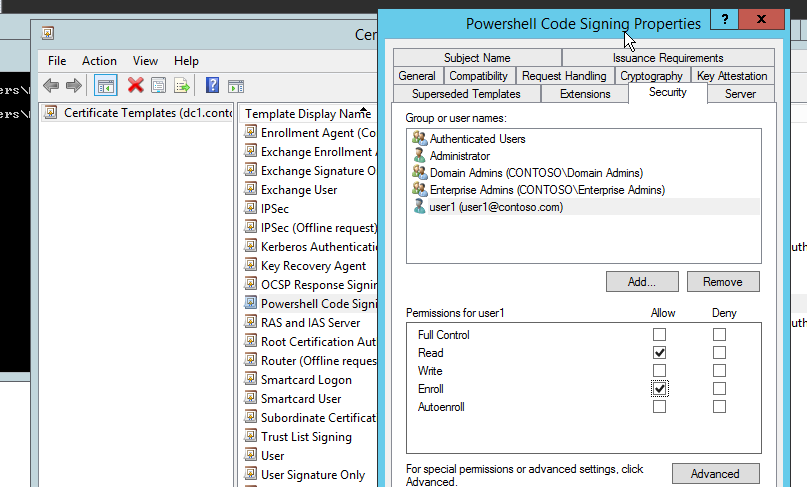
Give the Name of the template and certificate validity period. I give it Powershell Code Signing and the default validity period and renewal period. Then, click OK. See figure-10.
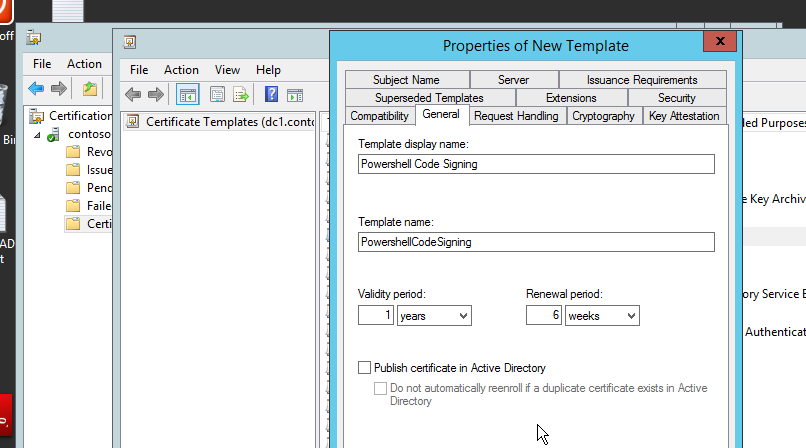
So far now, we have basically configured the code signing cerficate template. You can further configure according to your needs such as key usage, request handling. More about certificate template on TechNet article here.
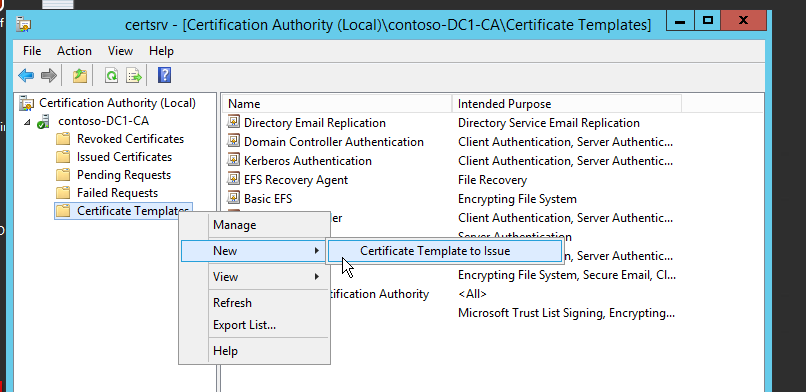
And we put this template on the list of certificates to be issued.
On the Certification Authority, right-click the “Certificate Templates” >> New >> Certificate Template to Issue. See Figure-11.
Now, we have setup CA role, initially configure CA and configure our template for code signing. They are only done on DC1 server where AD CS role is installed (I installed AD DS roles on the same computer also because of lack of resources)
On the Part-2, user1 will request our configured certificate from his Node1 computer and sign his script.
Next Part >> Part-2: Request the certificate the sign the script by user1

Great article. I will test it in my LAB.
BTW Links on the bottom of every chapter are broke, but links at the top are working fine.
TOP:
https://www.scriptinghouse.com/2016/08/how-to-digitally-sign-the-powershell-scripts-with-microsoft-ca-in-domain-a-step-by-step-guide-part-2.html
BOTTOM:
https://sysadminplus.blogspot.com/2016/08/stop-running-unsecure-scripts-how-to_21.html
Thanks for the point-out. Links are fixed.