2) Request the certificate the sign the script by user1
Go to >> Part-1:Install ADCS service and configure Code Signing Certificate Template
Go to >> Part-3: Configure GPO to allow only signed scripts and add user1’s certificate to trusted publisher group on domain computers
Go to >> Part-4: Run the test scripts
In the Part-1, we have configured AD CS role and configure certificate template. Now, it’s time that user1 request his certificate and sign his script. On the Node-1 computer with user1 logged on as domain user:
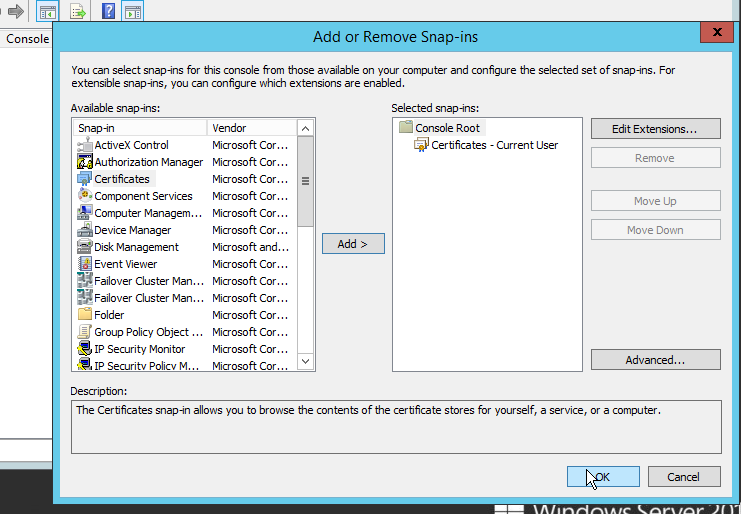
- In the Run box, type mmc and select “Certificates” from Add or Remove Snap-ins. See Figure-1.
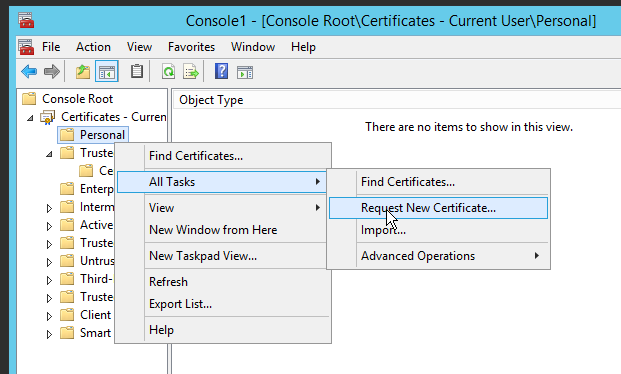
- In the certificate tab, right-click Personal >> All Tasks >> Request New Certificate. See Figure-2.
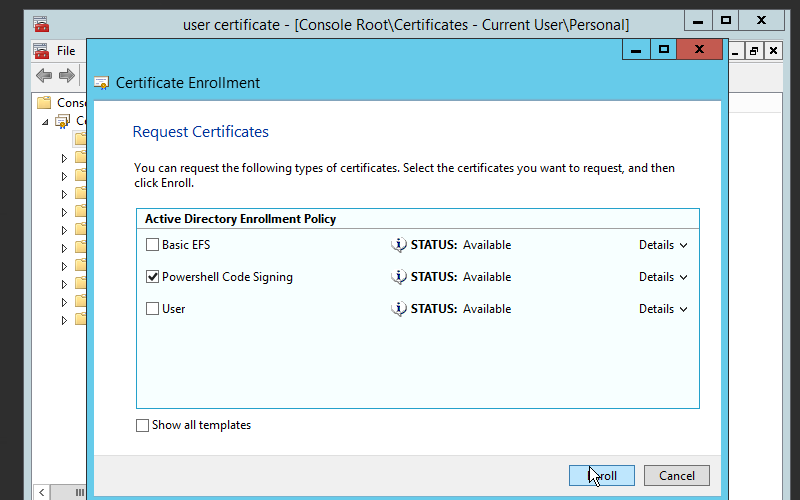
- Click Next and go until you find different types of certificates available on “Request Certificates” tab. Choose “Powershell Code Signing” and click “Enroll”. See Figure-3.
- If everything is working fine, you will see the certificate is enrolled and installed.
- Check user1’s enrolled certificate in certificate personal store. See Figure-5.
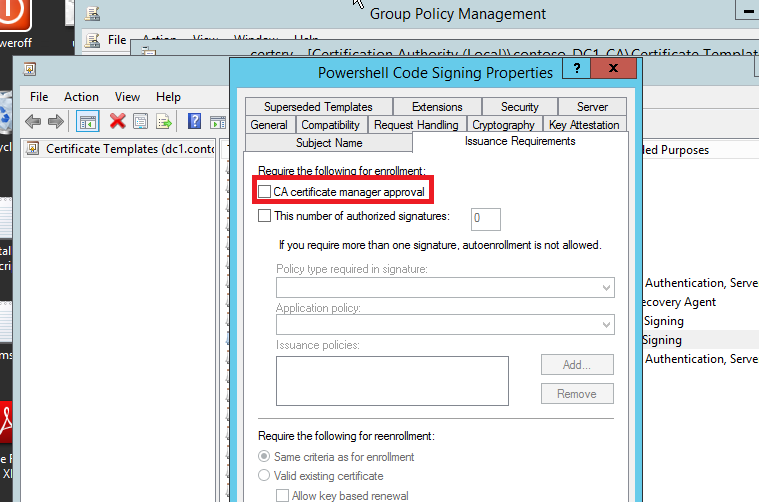
Note: If you turn-on “Certificate Manager” Approval in your certificate Template(see fig-4), then the certificate request will be shown as pending in “Certification Authority” console, rather then automatically enrolled to user1 computer. Certificate Manager Needs to approve the pending certificate to issue.
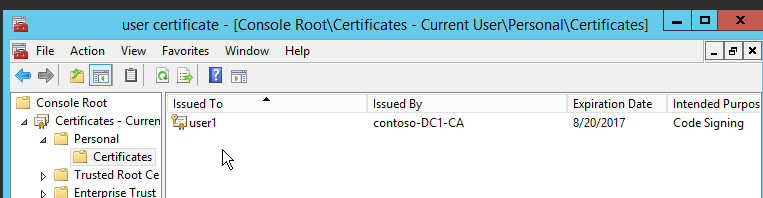
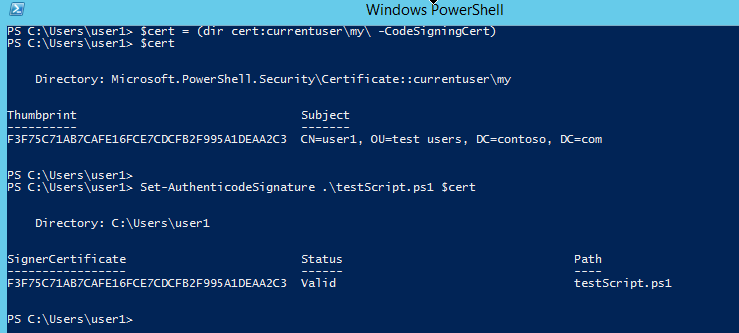
user1 now has the certificate to sign his script. The following powershell command will sign his script. But not only limited to scripts, the command can be used to sign other executable types such as: .exe, .vbs, .dll. The first command will fetch the certificate object from his certificate personal store and the second command will sign the script where “.testScript.ps1” is user1’s script.
$cert = (dir cert:currentuser\my -CodeSigningCert)
Set-AuthentiCodeSignature .\testScript.ps1 $cert
Upon successful signing, you will see the output similar to Figure-6.
On the first run of the script, it will prompt you for confirmation to run the script from the untrusted publisher. You can add this certificate to trusted publisher permanently and user1 certificate will be added to trusted publishers in certificate store. In next chapter, we will put this certificate to trusted publishers via Group Policy in advance so that user will be no longer prompted on the first run. See Figure-7.
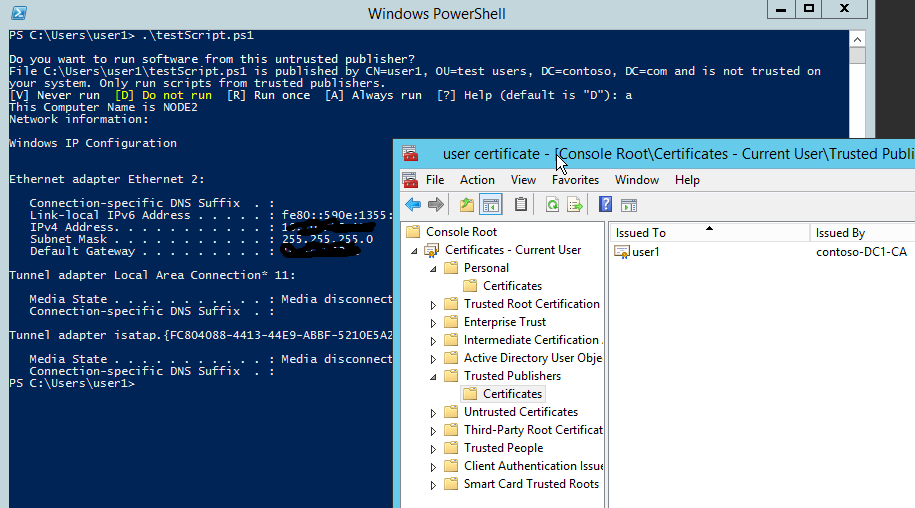
This is the Part-2 of the Series. In next chapter, we will be using GPO to automatically add user1’s certificate to trusted publishers group on domain computers. We will also force all the domain computers to run only signed powershell scripts.
